Internet censorship is a contentious topic all over the world today. While some advocate it as a safety net restricting access to the dark and illegal portions of the internet, others consider it to be merely a tool used by governments and authorities to conceal information from citizens for religious or political purposes.
China might have emerged as the poster boy, but almost every nation in the world censors internet access to some extent, even when the United Nations Human Rights Council has passed a resolution in 2016 declaring that online freedom is a basic human right that must be protected.
It’s not only countries which impose such limitations on their citizens.
Internet-based service providers also use geo-blocking to selectively provide content and access to users based on their geographic location.
For example, leading media streaming site Netflix filters content available to viewers based on their IP address, while popular cryptocurrency exchange and trading platform BitMEX geo-blocks users from restricted countries from logging into their website.
A familiar site for victims of Netflix's geo-blocking
The Ugly Side of VPNs
The concept of Virtual Private Network (VPN) has existed from as early as the 1990s, but the recent increase in internet censorship has seen a steady growth in the number of VPN providers over the last few years. One out
of every four internet users uses VPN today. The global VPN market is
expected to be valued at $35.7 billion by the end of 2022.
Unfortunately, centralized VPN services (specially the free ones) are plagued by a host of issues and vulnerabilities.
The biggest risk is the logging of data as it travels through the VPN tunnel. While the logged data might not contain any IP address, there might still be enough information to give away the true identity of the person, entirely defeating the purpose of using a VPN. Browsing data might also be collected to be sold off to 3rd parties. Even if the VPN service is completely scrupulous, an inadvertent VPN leak can expose the IP address or DNS name. NordVPN, one of the biggest names in the business, recently
admitted that they had suffered a data breach in 2018. And if security
issues are absent, there’s still the problem of network sluggishness a lot of us have faced while using centralized VPN services.
Decentralize the Internet?
Censorship resistance is a fundamental principle of blockchain technology, which strengthens the case for blockchain-based decentralized VPN networks. Substratum is possibly the best known crypto project working in this field. Unfortunately, there has been little progress in their work post ICO, and to make matters worse, the project got mired in controversy early this year. Similar blockchain projects like Skycoin and Maidsafe haven’t covered much ground either. However noble their intentions might have
been, crypto startups working in the decentralized internet space are yet to
prove their worth.
Decentralized internet had been solely under the purview of blockchain startups till now, but in a recent development, (centralized) VPN service provider X-VPN has announced that it is launching Tachyon Network, a blockchain based decentralized internet protocol, in association with V SYSTEMS, a blockchain infrastructure provider focused on database and cloud services. A relative newcomer in the ever-expanding world of VPN applications, X-VPN is used by over 50 million people worldwide. X-VPN
maintains a transparent logging policy, whereby neither browsing data nor IP address is recorded by the app. It provides IPv6/DNS leak protection, and offers secure connection to 33 countries. With an average rating of 4.4/5 on Android app store, X-VPN can be considered to be one of the more popular centralized VPN service providers out there today.
V SYSTEMS is also a relatively new entrant in the world of blockchain, having launched its native token VSYS earlier this year. V SYSTEMS’ blockchain uses a novel consensus mechanism called Supernode Proof of Stake (SPoS), which aims at delegating the power of creating new blocks to supernodes, while maintaining decentralization through the process of Cold Minting. Tachyon is the first DApp to be developed in V SYSTEM’s ecosystem. Though they are mainly focused on Decentralized Finance (DeFi) applications, a decentralized mobile internet network is also part of their long term vision, and that is probably a major impetus behind the fruition of this partnership.
What’s Tachyon?
Tachyon Protocol is building a transparent, stable, fast and decentralized internet protocol, by combining the features of blockchain, Distributed Hash Table (DHT), User Datagram Protocol (UDP) and cryptographic encryption, as described in their whitepaper. They believe that the privacy and security issues associated with centralized VPN systems stem from the internet protocol definition itself.
According to Tachyon, in order to implement a robust, fast and secure VPN, the current TCP/IP protocol stack has to be completely restructured.
Not only will it solve the problems related to centralized VPN services, but a host of other issues as well which make the existing TCP/IP architecture outdated and inefficient when it comes to providing the speed and reliability required to support Web3.0 applications.
So what’s the Issue with TCP/IP?
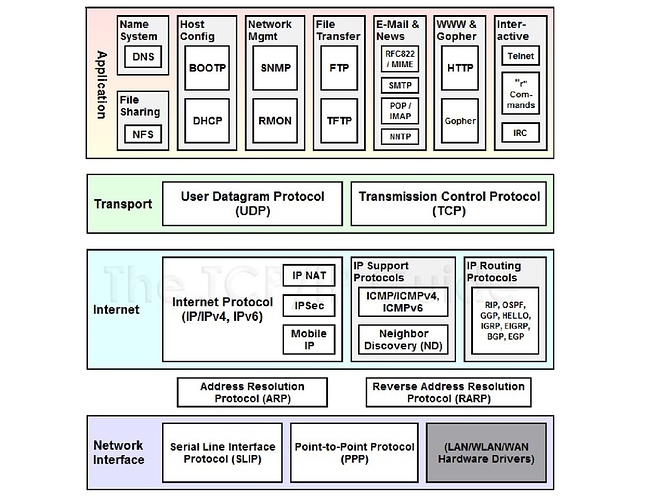
To set the context, the Internet protocol suite is a set of communication protocols which govern how network devices communicate over the internet. It consists of 4 different layers. Though TCP and IP are actually 2 distinct protocols running on the Transport
layer and the Internet layer respectively, the term ‘TCP/IP’ generally refers to the entire internet protocol suite.
TCP (Transmission Control Protocol) defines how applications create communication channels across a network, and manages how messages are fragmented and reassembled during transmission and reception. IP (Internet Protocol) dictates how packets are addressed and routed in order
to make sure that they reach the correct destination. In tandem, TCP and IP are the foundational protocols of the entire suite of internet protocols.
The other 2 layers are the Data Link layer and the Application layer – the former manages the transmission of data bits through the hardware components of the network, and the latter defines the communication
protocols and interface methods used by the network host.
The ubiquitous TCP/IP Protocol
TCP/IP based internet communication has been the norm for over four decades now, but as new technologies are coming to the forefront, kinks are being observed in its armour. For example, IP addresses are often tied to physical addresses, and once hackers gain access to an individual’s identity, various means of social engineering can be employed to commit fraudulent acts. Even HTTP, the most abundantly used protocol for data transmission in the application layer, is unencrypted and extremely vulnerable to hacking. Moreover, when a network running TCP becomes
congested, the three-way handshake, acknowledgement and congestion control mechanisms (which are all integral to TCP) only lead to bandwidth wastage and further congestion.
Tachyon’s Architecture
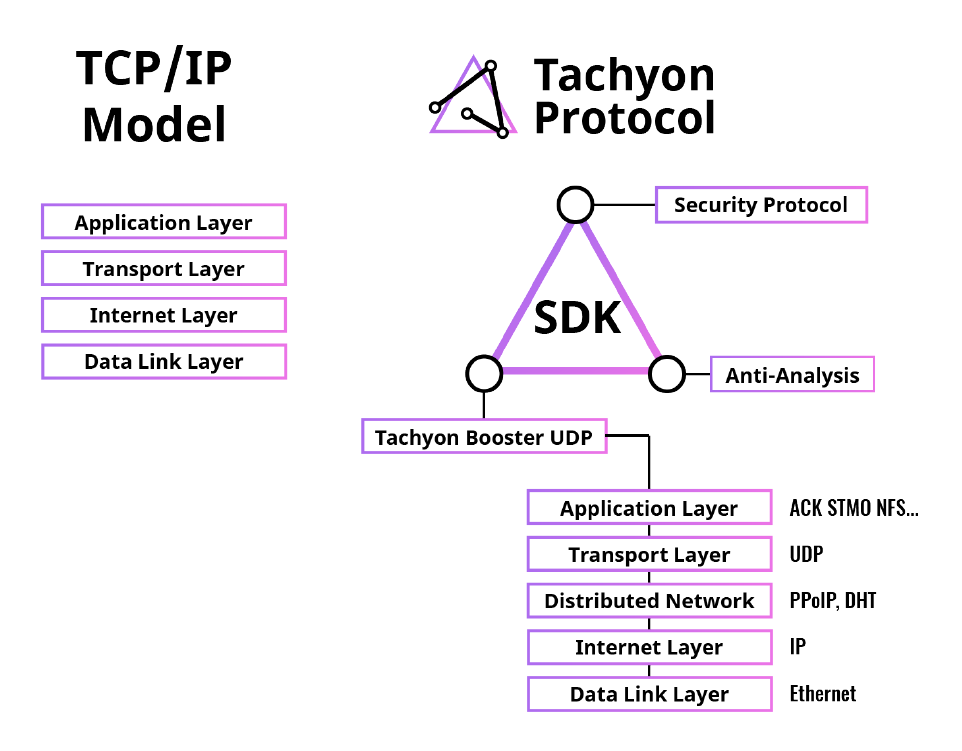
Tachyon’s architecture models aims at completely overhauling the existing TCP/IP model, and providing addition security and privacy features.
Tachyon's Architecture Overview
Tachyon Booster UDP (TBU)
In the Tachyon environment, TBU is the bottom layer protocol which
will replace the Internet, Transport and Application layers of the TCP/IP
model.
Tachyon claims that when used in conjunction with real-time Optimal routing, TBU can increase transmission speed by 2x to 10x in a centralized network, and achieve over 90% connection success rate in a complex network environment.
Internet Layer – Tachyon Protocol uses a combination of Point-to-Point
Protocol (PPP) and blockchain technology to facilitate the large-scale collaboration of Peer-to-Peer (P2P) networks. This eliminates the need of a central server, and offers anti-censorship through decentralization. To ensure robustness of the P2P networks, a Tachyon DHT based on Kademlia routing protocol is implemented.
Transport Layer – Tachyon uses UDP instead of TCP in the transport layer. UDP offers superior throughput and has less overhead compared to TCP, which improves transmission efficiency.
Application Layer – The application layer is redesigned to support the UDP in the transport layer. The optimizations include Forward Error Correction (FEC) to reduce packet loss, and bandwidth auto-scaling techniques to maximize the throughput efficiency.
Tachyon Security Protocol (TSP)
TSP is the security component of Tachyon’s ecosystem. Network
sniffing and Man-in-the-middle attack are arguably the biggest threats to P2P networks today.
TSP uses AES to encrypt the connection, and a combination of hash algorithms (such as HMAC, SHA2 and Keccak) to ensure that messages would be ignored if the communication channel gets disrupted.
Other safeguards include adding redundant data to transmissions, and automatically renegotiating the encryption key after a certain amount of data has been transmitted.
TSP also simulates the feature state of the communication protocol (UDP, TCP, HTTP, HTTPS, FTP and SMTP) in order to conceal the real information and avoid data exposure. This simultaneously prevents hackers from
finding the characteristics of the Tachyon traffic, and firewalls from detecting the traffic. This practice is followed by X-VPN’s application as well.
Tachyon Anti-Analysis (TAA)
Tachyon Network uses TAA to reduce the risk of single node capture
attack in its decentralized network. It involves using concurrent multi-path routing and multi-relaying scheme. Data is broken down into multiple IP packets and transmitted through different channels simultaneously. If any channel is intercepted, the hacker can retrieve only a portion of the message. Furthermore, messages are relayed through multiple nodes so that it’s extremely difficult for any attacker to determine the actual target node. As the number of nodes in the network increase, the difficulty of intercepting messages or monitoring the network increases exponentially.
Tachyon SDK
Most of the blockchain networks out there today use conventional TCP/IP based networking. To ease the transition to Tachyon’s internet protocol and reduce the integration expense, Tachyon has developed a SDK which blockchain networks can integrate with their technological stack.
Tachyon Ecosystem
Tachyon Protocol is also implementing an open, P2P market network where nodes provide services to each other. Their ecosystem will support 3 different types of nodes – Client nodes, which initiate connections; Provider nodes, which relay the traffic; and Business nodes, which purchase resources and services from other nodes. Tachyon’s native currency is the IPX token, which resides on the V SYSTEMS blockchain. Provider nodes will have to stake a certain amount of IPX tokens as a security deposit. IPX will also be used as the medium of payment by the participants in Tachyon’s ecosystem.
Tachyon Protocol plans to support multiple industries and sectors through its protocol stack and SDK.
Tachyon VPN marks their inception, which will also serve as a litmus test of the robustness of their solution. This will be followed by the integration of their protocol stack into V SYSTEMS as the transport protocol. In the near future, they are targeting DeFi, Internet-of-Things (IoT), and Decentralized Storage industries among others.
Tachyon claims that their protocol can provide more advanced security and privacy protection mechanism while reliably connecting a massive
number of nodes – features which both the DeFi and IoT sectors would require in the near future. Moreover, their protocol has the same underlying foundations as the IFPS protocol, which is used for sharing and storing data in distributed file systems. Tachyon will provide an extra layer by encrypting the contents both during transmission and storage.
Parting Thoughts
Blockchain startups working in the field of decentralized internet haven’t really made a mark yet. Tachyon Protocol is trying to push the boundaries by re-structuring the TCP/IP model itself through their own protocol stack. It’s a radical idea, and honestly, seems to be a tall claim from another startup in the block(chain) for now.
One factor which sets Tachyon apart from other projects is that they have been collaborating with both X-VPN and V SYSTEMS since 2016, to improve fundamental internet infrastructure technologies. Their combined technical expertise can give Tachyon an edge over the other players in this field. Moreover, their partnership with X-VPN automatically provides them access to X-VPN’s worldwide user base of over 50 million.
That said, the shared R&D and the user base can only serve as a stepping stone for Tachyon. Moreover, both X-VPN and V SYSTEMS are also relatively new entrants in their respective fields. Whether users adopt or shun their protocol will finally depend on how much value it actually adds to Web3.0 DApps. Till then, it’s all on paper.